Service to Service authorization made as easy as SSO
Authorizing API service traffic accurately is a critical challenge in enterprise infrastructure. Traditional approaches like IP allowlists lack precision and can break internal dependencies, while user-level SSO fails to prevent unauthorized service-to-service access.




Block prompt and code injection attacks and data leakage
Protect critical enterprise systems from abuse
Control costs and protect against overspend
Ensure secure and compliant AI operations
Wallarm reduces the risk of unauthorized access to internal services
Differentiating internal from customer traffic is critical yet challenging for modern software platforms. Legacy methods often fail to provide the granularity needed for secure and efficient API authorization. Wallarm solves this complexity with precise, context-aware blocking and monitoring, ensuring seamless protection without breaking internal dependencies.

Granular API Access Control
Traditional IP allowlists and static rules create blind spots and operational overhead. Wallarm enforces precise, policy-driven access control at the API level, ensuring only authorized services communicate.

Context-Aware Traffic Validation
User-level SSO does not prevent unauthorized service-to-service interactions. Wallarm dynamically verifies API requests based on identity, behavior, and contextual signals, reducing risk without disrupting workflows.

Seamless Enterprise Integration
Security shouldn't slow down innovation. Wallarm integrates natively with cloud, on-prem, and hybrid infrastructures, providing real-time visibility and automated enforcement without modifying your existing architecture.
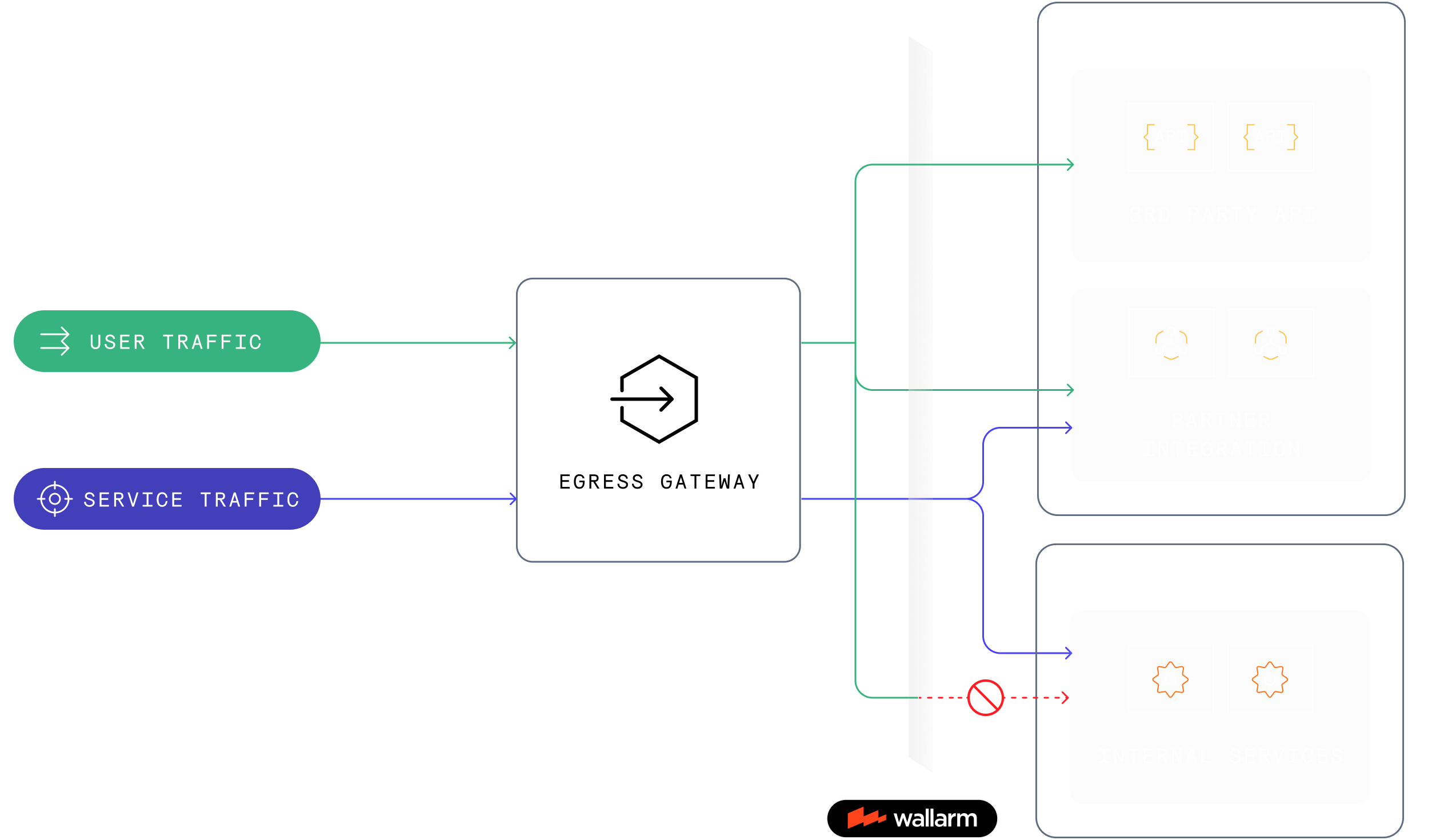
Identify applications accessing internal services
Wallarm identifies requested applications and their endpoints in egress traffic, including authentication, parameters, sensitive data types, and known vulnerabilities.
This doesn't require modifying source code and easily scales to hundreds of thousands of hosts.


Block unauthorized access to internal service in real-time
Implement granular rules to precisely block traffic from customer apps accessing internal service with no effect on other services. Use any request context parameter to trigger an action and block or monitor malicious activity.




Application Security Posture Management

Continuous Application Discovery
Automatically map all APIs—internal, external, shadow, and orphaned—to eliminate blind spots. Gain deep visibility into every API call to reduce exposure and enforce security policies effectively.

Real-time Threat Prevention
Detect and block live attacks targeting your APIs, including credential stuffing, abuse, and unauthorized access. Stop threats before they impact critical business functions.

Automatic Vulnerability Detection
Continuously identify API-specific vulnerabilities by mapping CVEs and business logic flaws directly to your API ecosystem, enabling rapid remediation without disruption.

Live API Monitoring & Drift Detection
Maintain real-time visibility into API changes, newly exposed endpoints, and misconfigurations. Detect and prevent security drifts before they become exploitable.

Behavioral Anomaly Detection
Analyze API usage patterns to identify abnormal behaviors such as data exfiltration, abuse, or unauthorized automation, ensuring rapid response to potential threats.

Holistic API Security Posture
Achieve complete API security visibility with automated detection, monitoring, and protection—without manual overhead. Align security with enterprise-scale infrastructure effortlessly.
Trusted by Security & DevOps Teams Globally
Fortune 500 and many other of the world’s largest tech companies rely on Wallarm to protect their APIs.
With Wallarm, we've been able to scale API protection to the scale we need and manage with our infrastructure as a code approach.
3000+
protected APIs and apps

Ready to protect your APIs?
Wallarm helps you develop fast and stay secure.