Stop Account Takeovers Instantly
Wallarm's AI-driven analytics spot emerging takeover patterns in real time, session-level controls neutralize compromised access, and SIEM integration delivers operational alerts and dashboards.

Trusted By





Book Your API Security Demo Now
Wallarm's AI-driven analytics spot emerging takeover patterns in real time, session-level controls neutralize compromised access, and SIEM integration delivers operational alerts and dashboards.

Trusted By





Account takeover attacks exploit legitimate credentials and session tokens, leading to fraud losses, data theft, and regulatory fines. With attack sophistication increasing and consumer trust declining, traditional security tools that only block individual requests or IP addresses fall short.
Attackers easily bypass IP-based blocking by rotating addresses, and request-level filtering misses session-wide attack patterns. Organizations need session-level protection that stops the attacker, not just individual malicious requests.
Block Sophisticated Attacks Across All Channels
Stop account takeover before it impacts your bottom line. Wallarm detects credential stuffing, session hijacking, and other sophisticated techniques across web, mobile, and API channels. Our AI-based detection minimizes false positives while ensuring real threats are neutralized immediately.
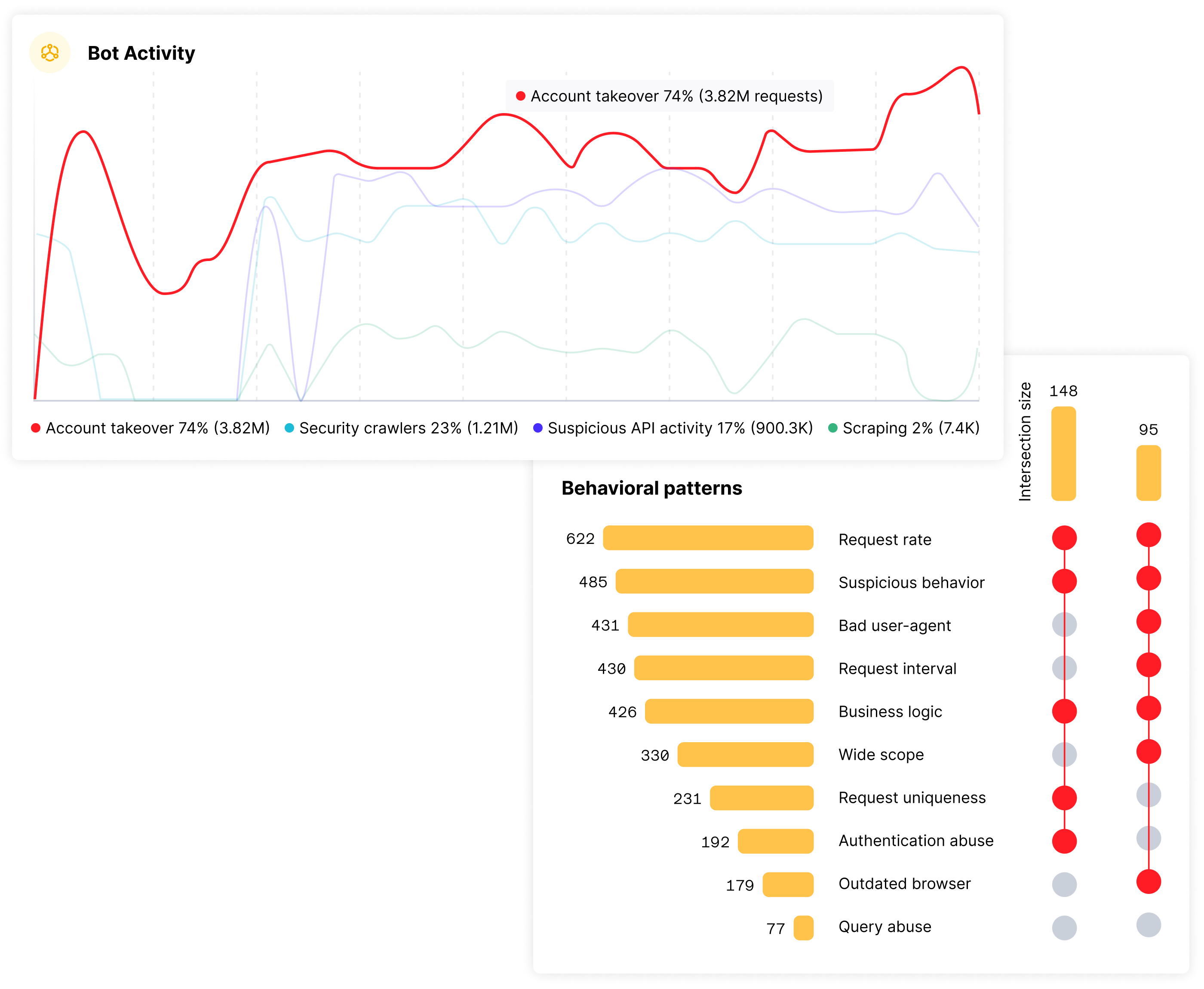
Block the Attacker, Not Just the Attack
Unlike traditional tools that only block individual requests or IP addresses, Wallarm blocks entire compromised user sessions. When attackers rotate IP addresses or change tactics, they remain blocked because we target their session identity. This prevents lateral movement and stops persistent attacker footholds within minutes.
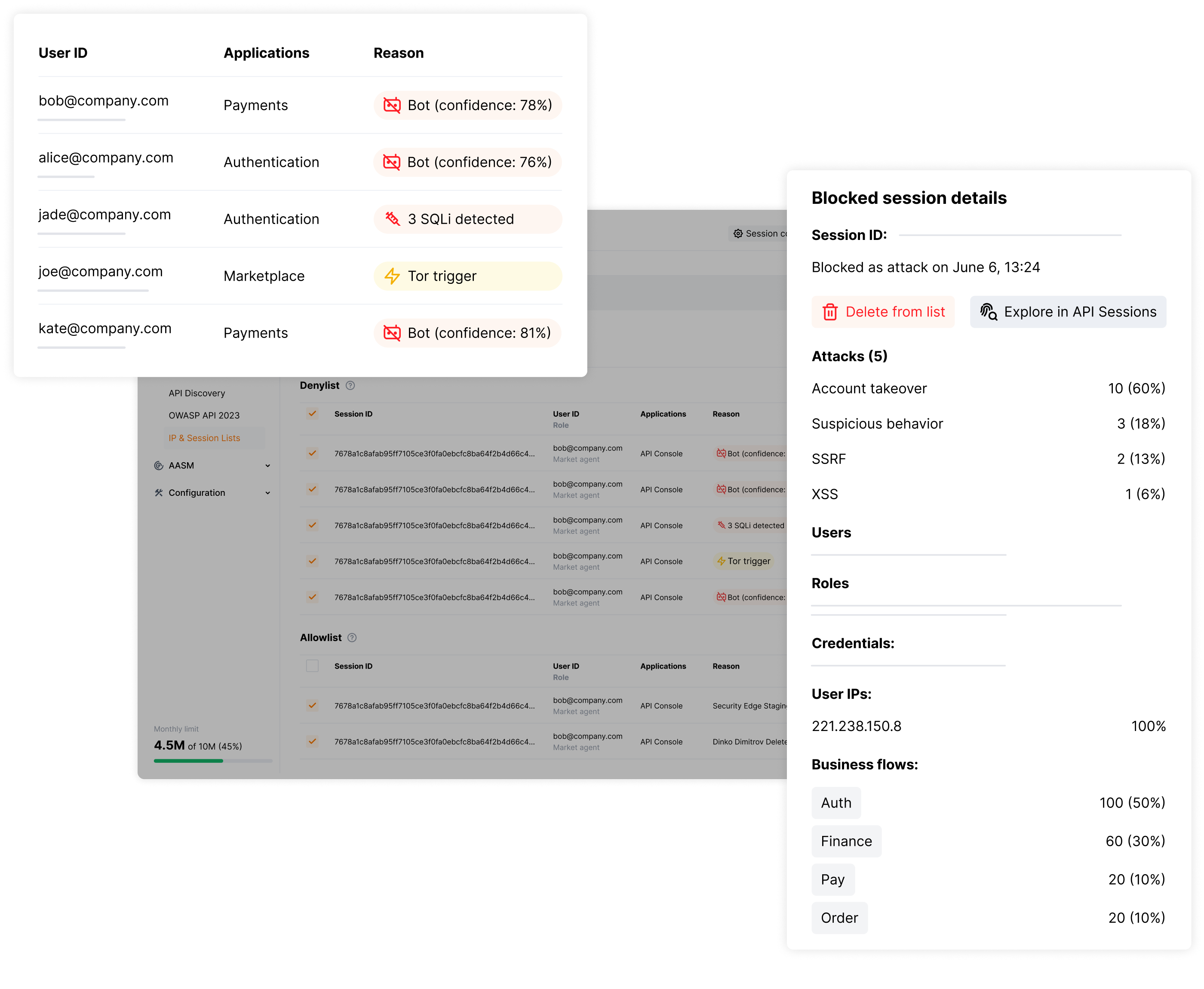
Full Visibility Into Every Attack
Track every user session from origin through completion, correlating events across business transactions and applications. Identify takeover root causes, quantify potential losses, and generate executive-ready reports that demonstrate security ROI and risk mitigation.
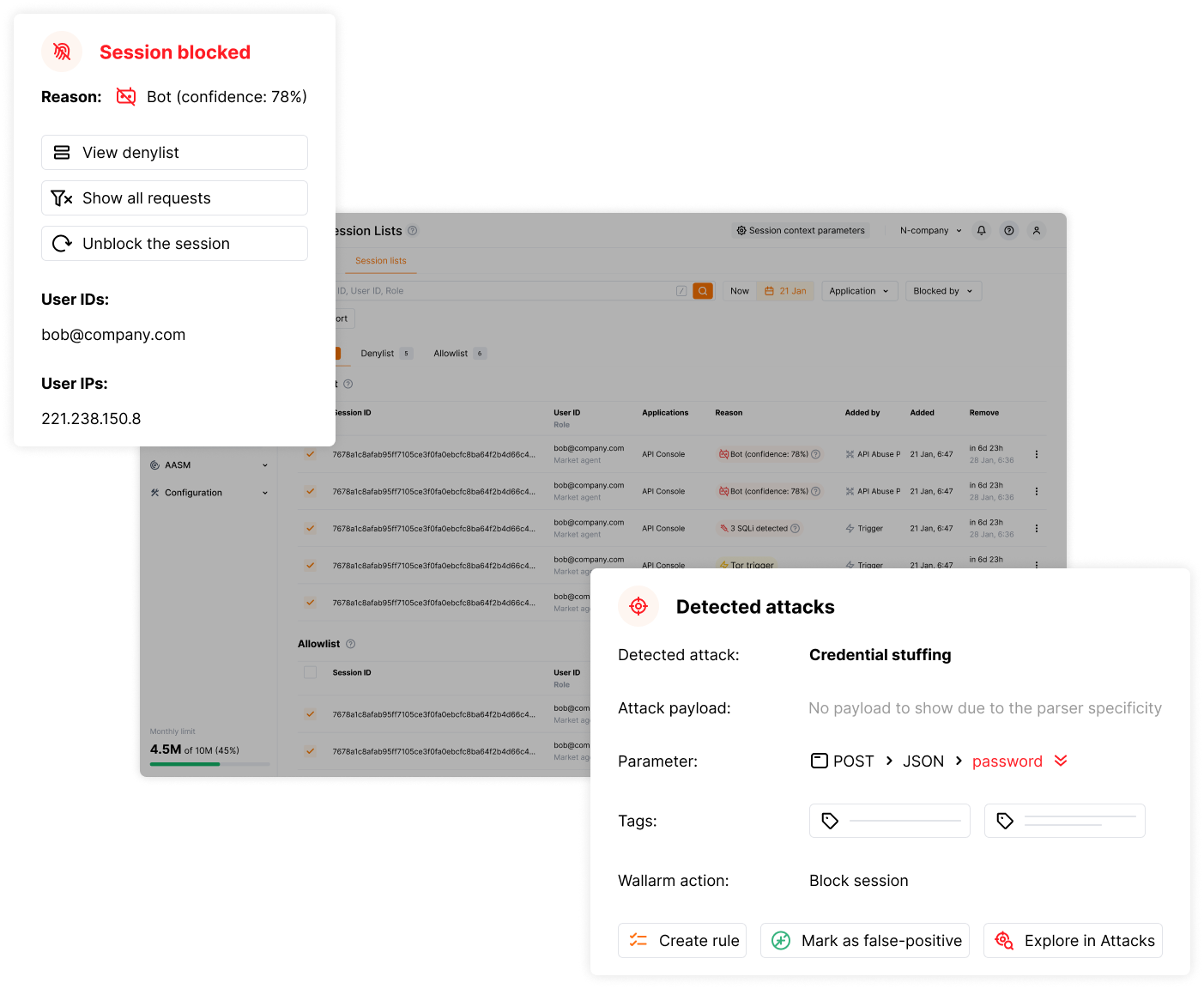
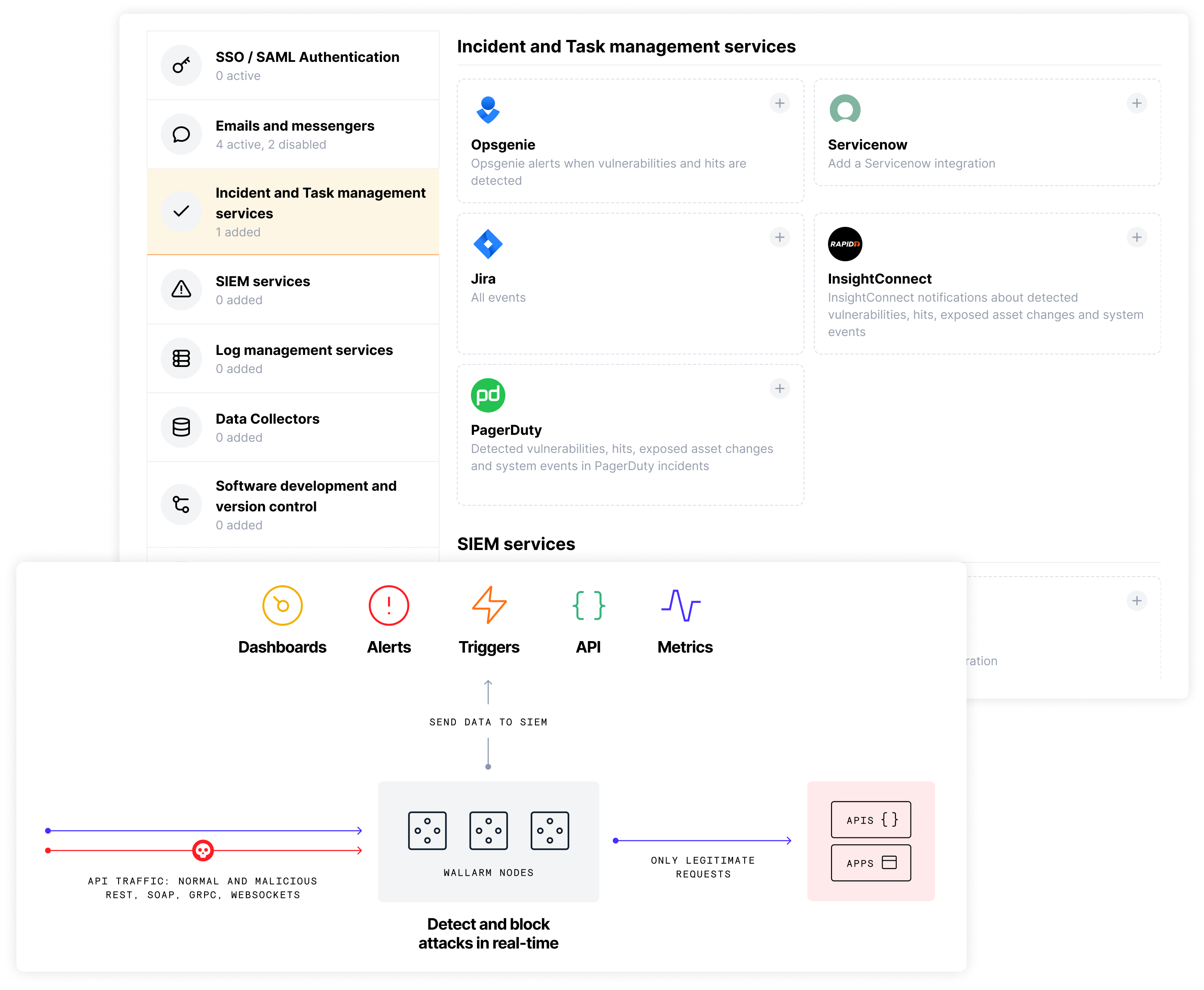
Automated Response and Executive Reporting
Deliver structured ATO data directly to your SIEM platform and trigger automated response playbooks. Native integrations with Splunk, QRadar, Elastic, and SOAR platforms ensure your security operations center gets actionable intelligence, not just alerts.
Attackers don’t care that you watch them, they only care if you stop them. That’s why Wallarm is the preferred choice for Security teams seeking unparalleled protection and prevention capabilities.
#1
In customer reviews
160K+
APIs protected
Billions
APIs requests protected, daily
I would absolutely recommend Wallarm, in a heartbeat. They do what they say on the tin – meaning what they say they can do, they really do.
