Don't Just Secure Your APIs. Secure Your Revenue
Wallarm connects API security to your bottom line. Pinpoint your most critical, revenue-driving APIs and shield them from business logic attacks that drain your profits.

Deploy in minutes

Trusted By





Wallarm connects API security to your bottom line. Pinpoint your most critical, revenue-driving APIs and shield them from business logic attacks that drain your profits.


Trusted By





In 2025, business-logic attacks account for 27% of all breaches. Attackers target APIs that handle critical functions, such as payments, authentication, user management, and other business-specific operations, to find and exploit vulnerabilities.
Breaches of business-sensitive APIs have driven global losses of up to $87 billion annually, with automated abuse alone costing $17.9 billion. Flawed business-logic APIs have exposed tens of millions of user records and incurred regulatory fines up to €10 million per violation under GDPR.

Without transaction-aware revenue attribution and real-time financial insight, security teams remain blind to dollars at risk, unable to prove ROI or stop profit-draining attacks.
Traditional firewalls and request filters only catch known stateless exploits, while IP blocking fails against address rotation and signature engines lag on attacks on business logic. They miss business logic abuse, in-session fraud, and data scraping on revenue-generating APIs.

Identify sensitive business flows and APIs implementing them
Reveal critical business flows by identifying the API endpoints driving revenue and impacting board-level KPIs with Wallarm’s automated mapping of all APIs, including unmanaged shadow and deprecated endpoints.
Wallarm prioritizes protection of payment, authentication, and user-management flows by tagging sensitive endpoints, such as checkout and account creation, with business function and financial impact.


AI-driven detection of attacks on business logic
Wallarm employs AI-based behavioral analysis to detect anomalies in API interactions, uncovering and blocking sophisticated, multi-step business logic abuses that others overlook.
Wallarm safeguards revenue-critical APIs against all modern threats, including the OWASP Business Logic Abuse Top 10 and API Top 10, which can easily evade traditional WAF solutions.
Block the Attacker, Not Just the Request
Unlike traditional tools that only block individual requests or IP addresses, Wallarm blocks entire compromised user sessions. When attackers rotate IP addresses or switch tactics, they stay blocked because we target their session identity. This guarantees they cannot exploit sensitive business logic.
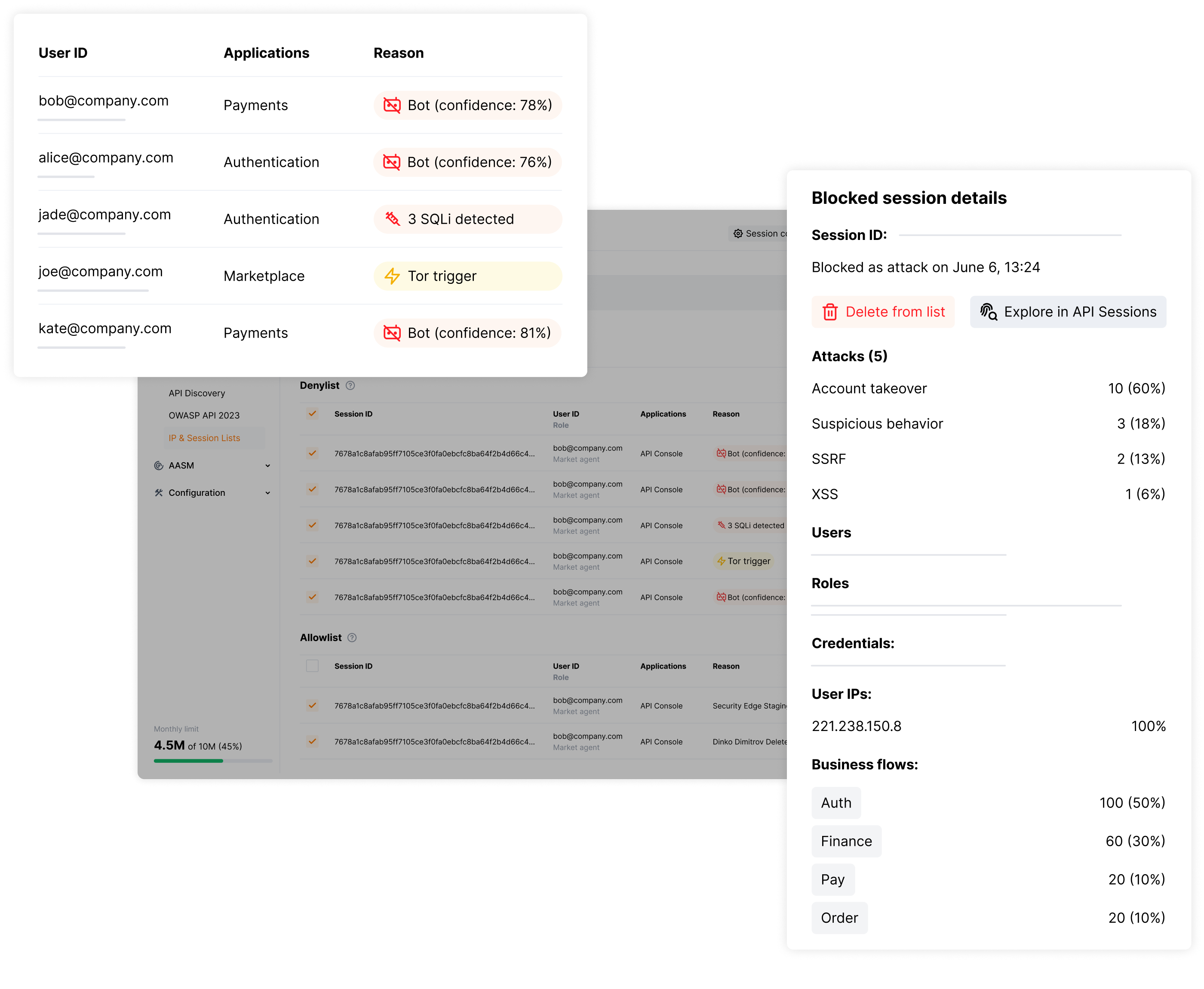

Track Revenue Impact of API Security
Prove API Security importance to top-line financial metrics by delivering executive-ready reports quantifying dollars protected and linking security efforts to the number of active users and revenue.
Utilize flexible dashboards for both financial and technical KPIs to demonstrate effective threat prevention and continuous risk reduction.
Talk To Sales