The Complete Guide to API Security in 2026
API security has become the most targeted attack surface. It’s no surprise, given how vulnerable APIs are. With 99% of organizations reporting API security incidents and over 50% of all exploited vulnerabilities tracked by CISA now being API-related, they have become the primary attack surface for adversaries. As enterprises rapidly deploy AI applications and agentic AI in production, all driven by APIs, API Security Platforms have become mandatory security controls.

Key takeaways
- API security is the practice of protecting Application Programming Interfaces (APIs), and the data and services behind them, from misuse, attacks, and accidental exposure. In simple terms, it ensures that only the right people and systems can call your APIs, that they can only do what they’re allowed to do, and that the data they access stays confidential, correct, and available when needed.
- API security is important because APIs provide direct, programmatic access to your most sensitive data and core business functions. Unlike attacks on traditional web interfaces, a vulnerable API lets attackers automate data extraction, bypass front-end controls, and exploit business logic at scale. A single misconfigured endpoint can expose millions of records or enable unauthorized transactions, often without triggering conventional security.
- Securing an API requires proactive and reactive controls. APIs should be developed with strong authentication (verifying who's calling), granular authorization (limiting what they can access), and input validation to block malicious payloads. Encrypt all traffic with TLS, enforce rate limits to prevent abuse, and log requests for monitoring and forensics. Organizations should implement API discovery, real-time blocking of attacks, and API security testing to ensure APIs are protected.
If you look at the major security breaches of the last three years (T-Mobile, Optus, Coinbase, Uber) you find a remarkably consistent pattern. An attacker identifies an endpoint that fails to check permissions properly, writes a script, and exfiltrates millions of records before anyone notices.
This is no longer an emerging threat; it is the reality of modern enterprise security. APIs have overtaken traditional web pages to become the primary mechanism for moving data across the open web. They are the fundamental backbone of our digital infrastructure, yet they remain systematically under-protected.
The gap between adoption and security has widened largely because development teams ship endpoints faster than security teams can review them. This speed often leads to "Shadow APIs"—undocumented endpoints that exist outside the security perimeter. When authentication is implemented but authorization is merely assumed, the result is an attack surface that expands every quarter while defenders struggle to map what they are supposed to be protecting.
To defend against this, we need to look beyond the code and understand the architecture itself. The vulnerability isn't just in how APIs are written, but in how they are designed to function.
What is an API?
An API (Application Programming Interface) is a set of rules that lets one piece of software request data or actions from another. It defines exactly what requests a system will accept, what parameters are required, and what it will return. Think of it as a contract: one system agrees to provide data, but only if the request matches a specific format.
Unlike a standard website, which sends HTML to be rendered for a human user, an API sends raw data (usually JSON) intended for a machine. This distinction is central to understanding API security.
Consider a weather app. When you check the forecast, your phone acts as a client. It sends a structured HTTP request to a server, such as GET /api/weather?location=California. The server replies with raw data containing temperature, humidity, and wind speed.
The reason this matters for security is that in a traditional web app, the server controls the interface and decides what buttons you see. In an API context, the client has direct access to the data and business logic. Without authentication and authorization, the weather service has no way of knowing if the request is coming from your mobile app or an attacker’s Python script; it simply answers any request that satisfies the requirements.
The technical foundation for this exchange is most often REST over HTTP, where a client targets a specific URL (the endpoint) using methods like GET to retrieve data, POST to create it, or DELETE to remove it. While REST is the most common API protocol, it is definitely not the only one.
Here is what an example REST transaction requesting user information actually looks like "on the wire":
Request:
Response:
This above snippet highlights a main concern of API security. The client presented a token (the key) and asked for user 12345, and the server returned the data.
But the critical questions, the ones that lead to breaches, remain invisible here. Does the owner of that token actually have the right to see User 12345? And more importantly, what happens if they change the ID to 12346?
If the API answers that second request without validating authorization, the system is vulnerable. This is why APIs are often described as "doors" into your application. And doors, if you aren't strict about who walks through them, inevitably become entry points.
Five Types of APIs
Not all APIs face the same exposure. Understanding these categories helps clarify the threat model.
- Open APIs: These are also called public APIs, may be commercial in nature, and are available to anyone, sometimes with registration or a license required. Twitter's API lets you build social media tools. Google Maps' API enables you to embed maps and calculate routes. OpenWeatherMap lets you pull forecast data. Stripe allows you to process payments. The barrier to entry is intentionally low: sign up, get credentials, start building.
Open APIs drive platform ecosystems. They turn API-based products into infrastructure that others build on. But they also face the broadest range of attackers. Anyone can register. Anyone can probe for weaknesses. Rate limiting and abuse detection become critical because you can't predict who's on the other end. - Partner APIs: These restrict access to specific business relationships. For instance, a hotel chain shares real-time inventory with travel sites, but not with the general public; a bank provides account data to approved fintech partners in accordance with contractual and regulatory frameworks; or a healthcare provider exchanges patient records with affiliated hospitals through private integrations.
Partner APIs involve legal agreements, security reviews, and controlled credential distribution. The attack surface is narrower as you need a business relationship to get access, but the data is often more sensitive. A compromised partner API can expose information that was never meant to leave the organisation - Internal APIs: Internal APIs are private APIs that exist only within an organisation's network. They connect microservices, link databases to applications, integrate HR systems with payroll, and shuttle data between internal tools. If you don't work there, you'll never see them. Often, they're not even documented outside the team that built them.
Internal APIs frequently have weaker security than external ones. The assumption is that network boundaries provide protection, so if you're inside the perimeter, you're trusted. That assumption breaks down when attackers gain initial access through other means, like phishing, compromised credentials, or vulnerable external services. Once inside, poorly secured internal APIs become highways for lateral movement. - Composite APIs: These combine multiple operations into a single call. When you complete an e-commerce checkout, the backend might verify inventory, reserve the item, process payment, update shipping, send a confirmation, and adjust analytics, all from a single request. The composite API orchestrates these calls so the client doesn't need to manage the sequence.
Composite APIs reduce round-trip and simplify client logic, but they concentrate risk. A flaw in the orchestration layer can expose multiple backend systems. And because they aggregate sensitive operations, they're high-value targets. - AI APIs: This is a rapidly emerging category. Every generative AI application and agent is connected via APIs. Unlike traditional APIs that access structured databases or business logic, AI APIs interact with complex models, often processing massive, unstructured datasets. Their unique security challenge lies in protecting the underlying model from theft or corruption and defending against prompt injection attacks, where malicious input is used to manipulate the model's behavior or extract confidential training data. Access control and rate limiting are crucial, but so is validating the nature and content of the inputs to prevent adversarial exploitation of the model's logic.
What is API security?
API security is the practice of protecting APIs, and the data and services behind them, from misuse, attacks, and accidental exposure. It ensures that only the right people and systems can call your APIs, that they can only do what they're allowed to do, and that the data they access stays confidential, correct, and available when needed.
That may sound straightforward, but successfully implementing these controls is not.
API security focuses on the APIs your organization exposes, whether they face the public, partners, or internal services. Those are the doors attackers walk through. In practice, securing APIs is never a single-team job. It spans development, identity, infrastructure, and monitoring. Network controls, such as throttling and rate limiting, sit beside identity-based controls and behavioural analytics. All of them have to work together because attackers only need one weak layer to get through.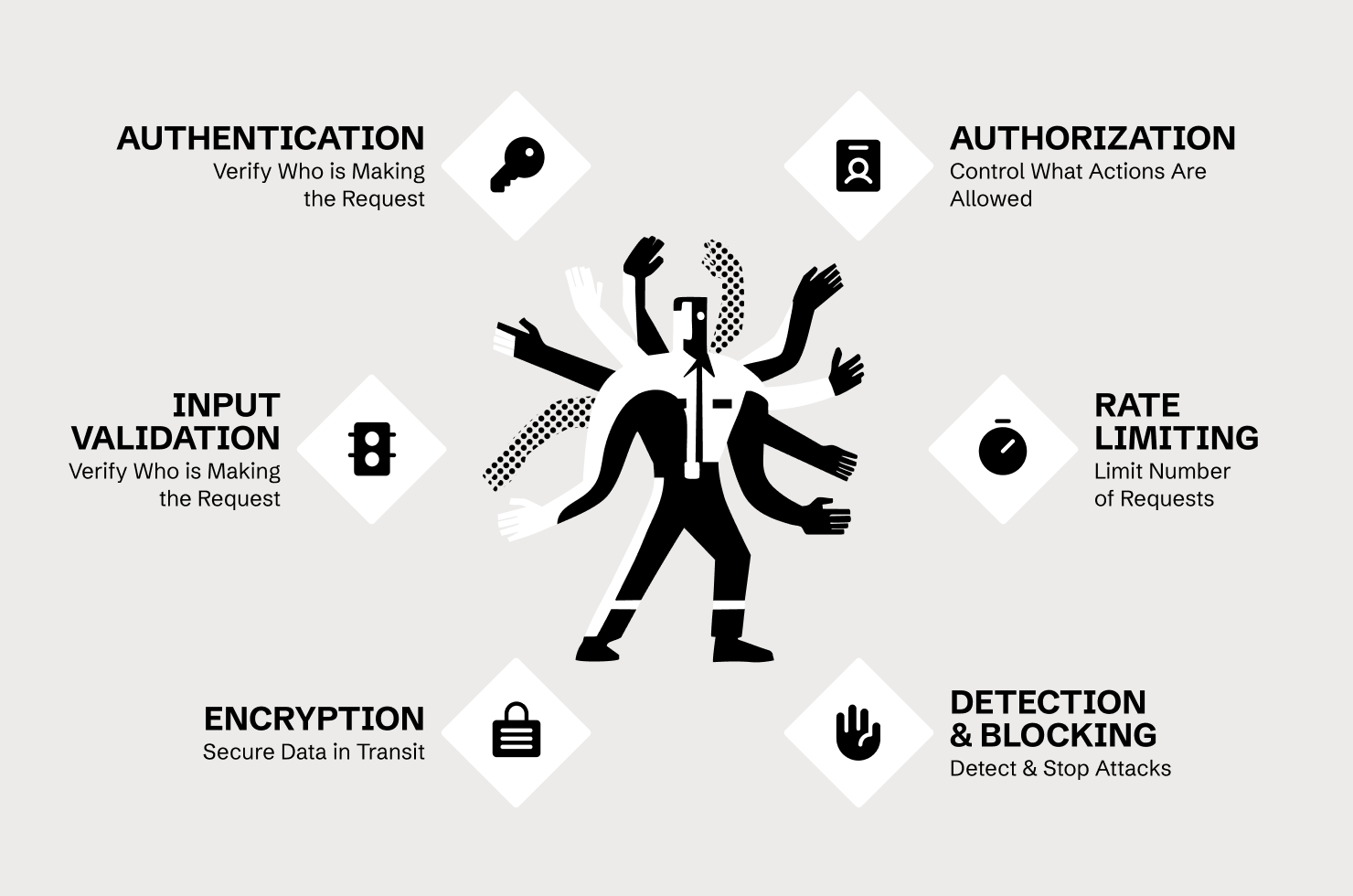
- Authentication: answers the question: Who is making this request? The API needs to verify identity before doing anything else. Common mechanisms include API keys (limited but straightforward), OAuth tokens (more complex, better suited for delegated access), and JWT (JSON Web Tokens, which carry encoded claims about the requester). Authentication failures—missing checks, weak credential validation, tokens that don't expire—are foundational vulnerabilities.
- Authorization: answers a different question: is this authenticated entity allowed to perform this specific action on this particular resource? Authentication tells you who someone is. Authorization determines what they can do. The distinction matters enormously. A valid user token doesn't mean that the user should access every record in the database. A partner credential doesn't mean that the partner can call every endpoint. Authorization failures are the most exploited category of API vulnerability, and we'll return to them.
- Input validation: ensures incoming data matches expectations. APIs accept parameters in URLs, headers, and request bodies, which are eventually processed by backend systems. If the API doesn't validate that a user ID is actually a number, or that a date field contains a valid date, or that a JSON payload doesn't include unexpected fields, attackers can inject malicious content. SQL injection, command injection, and mass assignment attacks all exploit insufficient validation.
- Rate limiting: controls how many requests an entity can make in a given timeframe. Without it, attackers can brute-force credentials, enumerate through every possible ID, scrape entire datasets, or overwhelm the service with traffic. Rate limiting is partially about availability—preventing denial-of-service attacks—and partially about detection. Abnormal request volumes are often the first signal that something is wrong.
- Encryption: protects data in transit. APIs should run over HTTPS, ensuring that network observers can't intercept credentials, tokens, and payload data. This is table stakes, but misconfigurations still happen—mixed HTTP/HTTPS deployments, improper certificate validation, sensitive data logged in plaintext.
- Detection & Blocking: This is the reactive layer of API security, designed to identify and stop attacks in real-time. It moves beyond simple signature matching to analyze user and application behavior, looking for anomalous patterns like credential stuffing, account enumeration, or business logic exploitation (e.g., BOLA attempts). Tools like next-generation Web Application and API Protection (WAAP) or dedicated API security platforms use AI and behavioral analytics to establish a baseline of 'normal' traffic. Once an attack is detected—based on abnormal request volumes, unusual call sequences, or deviations from the API's expected structure—the system must have the capability to immediately block the malicious requests, issue alerts, and provide detailed data for forensic investigation. This ensures an attacker's window of exposure is minimized.
Each of these layers can fail independently. An API might authenticate users properly, but authorise them incorrectly. It might validate input, but fail to rate-limit. It might encrypt traffic, but log tokens in plaintext. Defense requires getting all of them right, simultaneously, across every endpoint.
API Security vs Web Application Security
Security practitioners who grew up protecting web applications face a transition. APIs share infrastructure and some vulnerability classes with traditional web apps, but their threat models differ in ways that matter.
Different traffic patterns: Web applications serve HTML to browsers, rendered for humans who click links and fill forms. APIs serve structured data (JSON, XML, or Protocol Buffers) to applications—mobile apps, partner integrations, internal services. Human timing and behaviour don't constrain API traffic. A thousand requests per second is unusual for a human using a website; it's normal for an application calling an API.
Different attack surfaces: APIs are usually not rendered directly like web pages, but are called by browser-based apps, mobile apps, and other servers, so traditional web risks don’t apply in the same ways. In practice, most serious API attacks come from broken authorization (including object-level and function-level access control issues), injection into backend systems, mass assignment through extra request fields, and business logic abuse that misuses legitimate features in harmful ways. Traditional web application defenses focus on spotting obvious attack patterns in HTTP traffic and blocking known payloads, but more subtle authorization and logic flaws are harder to catch because the requests look like normal, well-formed API calls.
Different detection challenges: Web application firewalls (WAFs) were originally built to detect known attack patterns in HTTP traffic, such as SQL injection signatures, XSS payloads, and directory traversal attempts. They usually work by matching requests against signatures. Attackers constantly work to hide attacks via WAF bypasses. More sophisticated, modern WAFs work to separate human users from automated bots, which often attempt to emulate a browser or human behavior.
Signature-based detection for API attacks have similar drawbacks, and API attacks often contain nothing anomalous in any single request. A BOLA exploitation looks like a regular request with a different ID. Business logic abuse uses the API as it was designed, just not as it was intended. Credential stuffing sends valid-format login requests, often with different credentials. Signature-based detection doesn't help with these attacks. Behavior-based detection with APIs focuses on anomalies, instead of separating humans from bots.
The industry is converging: Gartner renamed its WAF market category to Web Application and API Protection (WAAP) in 2021, recognising that organisations need both capabilities. And the WAAP market definition now includes the capabilities in the API Protection category as well.
But 53% of organisations report that their WAFs and WAAP solutions can't detect fraud at the API layer. The convergence is happening in product marketing faster than in actual protection capability. API security requires behavioural analysis—understanding what normal looks like and flagging deviations—not just signature matching.
Why API security matters now
The urgency isn’t theoretical. The numbers tell a consistent story across every major security report.
As evidence of how normalised the problem has become, 84% of organisations experienced an API security incident in 2024, up from 78% the year before. This isn’t a niche problem affecting careless teams. It’s happening almost everywhere, and it’s accelerating.
What makes that trend worse is that the breaches don’t stop at a single hit. Around 57% of organisations suffered an API-related data breach within two years. More worrying is the repeat rate. 73% of those organisations had three or more incidents, and 41% had five or more. Attackers don’t find one weak endpoint and move on. They keep seeing them because the underlying conditions don’t change.
The growth curve explains why defenders keep falling behind. Active APIs sit around 200 million globally today, with projections approaching 1.7 billion by 2030. Every new API is another door that needs real authentication, real authorization, proper validation, and monitoring. Most organisations can’t accurately count all their APIs, so they can’t secure them comprehensively.
That lack of inventory spills directly into a visibility problem. Only 27% of organisations that believe they have complete API inventories actually know which APIs handle sensitive data. Shadow APIs, meaning undocumented endpoints created by fast-moving teams, legacy systems, or third-party integrations, are now normal. Security teams can’t protect what they don’t know exists.
Once visibility breaks down, attackers naturally move to the easiest, high-return path. About 27% of API attacks now target business logic. These are cases where intended functionality is used in unintended ways, including credential stuffing, fake account creation, scraping, referral abuse, and promo farming. The API isn’t “broken” in the classic sense. It’s doing exactly what it was built to do, just not under adversarial pressure.
The hardest part is that none of this looks noisy at the surface. API attacks often mimic legitimate traffic, with valid endpoints, correct tokens, and well-formed requests. The difference between a user checking their account and an attacker enumerating through customer IDs is the pattern over time, not a single suspicious payload. Signature-driven tools don’t see that.
What tips the balance further is speed. Web attacks usually require human interaction, such as clicking, filling out forms, and completing CAPTCHAs. API attacks are automated from the start, so a script can test thousands of IDs per second and harvest data faster than any human-paced review cycle can respond. Wallarm’s own API Honeypot experiment showed that an API attacker can siphon off 10M user records in under 1 minute. The increased adoption of generative AI by attacks drives scale exponentially. It’s not just attack automation, but decision automation. With AI, attackers can effectively multiply high-speed sophisticated attacks.
API Protocols
While REST is the most widely deployed type of API, there are other well-established protocols that need to be considered. Different protocols (REST, SOAP, GraphQL, gRPC, Websocket) impact how API security should be applied and implemented. Streaming protocols, such as gRPC, and data-centric protocols, such as GraphQL, introduce their own unique security threats and attack vectors.
For example, GraphQL, due to its flexible querying capability, can be prone to resource exhaustion attacks if queries aren't properly validated and rate-limited. Each protocol, with its distinct architectural and operational nuances, requires specialized security considerations to address potential vulnerabilities and defend against tailored exploitation techniques.
API Protocol Comparison
Comparing REST, gRPC, and GraphQL API Security
At a high level, REST, GraphQL, and gRPC APIs all aim to expose application functionality safely to consumers, but the way they’re built fundamentally changes how they need to be secured. REST APIs tend to map cleanly to HTTP semantics, which makes them the most familiar and, in many ways, the easiest to protect. Standard controls like TLS, authentication headers, rate limiting, and per-endpoint authorization align naturally with REST’s resource-based model. That same clarity also makes REST APIs easier to inventory and monitor: endpoints are explicit, methods are well understood, and many security tools natively speak HTTP.
GraphQL flips that model on its head. Instead of many discrete endpoints, GraphQL typically exposes a single endpoint that accepts highly flexible queries. That flexibility is powerful, but it complicates security. Traditional controls like endpoint-based allowlists or per-URL rate limits lose precision when every request hits the same path. GraphQL security must account for query depth, complexity, and resolver behavior to prevent abuse such as expensive nested queries or data overexposure. Authorization also shifts from “can you call this endpoint?” to “are you allowed to access this specific field on this object?” which requires much tighter integration between schema design, resolvers, and access control logic.
gRPC introduces a different set of considerations altogether. Built on HTTP/2 and binary Protocol Buffers, gRPC is optimized for high-performance service-to-service communication, but that efficiency can make security visibility harder. Traditional HTTP inspection tools may struggle with binary payloads, and endpoint discovery often depends on .proto definitions rather than URLs. Securing gRPC APIs typically emphasizes strong mutual authentication (mTLS), strict service identity, and well-defined authorization at the method level. While gRPC’s structured contracts enable precise controls, they also demand tooling and processes that understand the protocol natively, otherwise, security risks can remain invisible despite strong cryptography.
With different protocols, the fundamentals don’t change—authentication, authorization, and abuse prevention still matter—but the implementation does. Treating GraphQL like REST or gRPC like plain HTTP creates blind spots. Effective API security requires aligning controls to each protocol’s interaction model, data exposure patterns, and operational realities, rather than forcing a one-size-fits-all approach.
API Vulnerabilities: The OWASP API TOP 10
The OWASP API Security Top 10 is a globally-recognized standard that highlights the most critical security risks with APIs today. It is a foundational awareness resource for developers, security architects, and penetration testers, providing a concise list of common and impactful vulnerabilities that result from design and implementation flaws. For API security practitioners, the list is useful because it helps prioritize mitigation efforts and testing strategies, ensuring that teams focus their limited resources on preventing the most frequently exploited and severe API security issues, such as Broken Object Level Authorization (BOLA) and Security Misconfiguration.
- API1:2023 (Broken Object Level Authorization): To address BOLA, detect vulnerabilities in both development and production, and consider using an inline API security tool to block attacks, especially when immediate code fixes are challenging. Risk Rating: 6.0
- API2:2023 (Broken Authentication): Start with detective controls to detect and block attacks, assess API vulnerabilities, prioritize high-risk ones, and implement fixes. If you don't control the app, collaborate with vendors with evidence and priorities. Risk Rating: 8.0
- API3:2023 (Broken Object Property Level Authorization): Identify vulnerable API endpoints, instruct developers to fix issues, and report third-party vulnerabilities. An inline API security tool can provide protection when quick fixes aren't feasible. Risk Rating: 5.3
- API4:2023 (Unrestricted Resource Consumption): Create a threat model for resource consumption, set external limits, and make risk mitigation decisions even without direct control over application code. Risk Rating: 8.0
- API5:2023 (Broken Function Level Authorization): Restrict function access in the code, maintain good API hygiene, and consider monitoring and blocking tools for better mitigation. Risk Rating: 8.0
- API6:2023 (Unrestricted Access to Sensitive Business Flows): Understand your business flows, use automated tools sparingly, employ blunt-force approaches, and maintain good API governance. Risk Rating: 5.3
- API7:2023 (Server Side Request Forgery): Ideally, restrict at the resource-fetching mechanism. If not, apply controls at the network or application layer, or use a dedicated tool to block SSRF attacks. Risk Rating: 5.3
- API8:2023 (Security Misconfiguration): Implement good security governance, create API specifications, and prioritize where to apply resources to eliminate misconfigurations. Risk Rating: 9.0
- API9:2023 (Improper Inventory Management): Begin by performing API discovery to improve documentation, incorporate API specifications into your development process, and request them from vendors to manage inventory properly. Risk Rating: 5.3
- API10:2023 (Unsafe Consumption of APIs): For APIs you control, implement best practices and evaluate against a checklist. For third-party APIs, validate their compliance with your checklist and establish a response plan for non-compliance. Risk Rating: 7.0
- Injection (formerly API8:2019): Injection attacks remain the most dangerous threat for APIs. Be especially aware of their risk and take proactive measures to prevent them. Risk Rating: 9.0
API Security Standards and Compliance Frameworks
Compliance doesn't equal security, but it does establish a baseline. If you're handling payment data, health records, or personal information from EU residents, the relevant framework isn't optional and each one has implications for how you build and secure APIs.
The PCI Data Security Standard (DSS) applies to any system that processes, stores, or transmits cardholder data. For APIs, this means encrypted transmission (TLS 1.2 minimum), strong authentication, access logging, and regular vulnerability assessments. If your payment API doesn't meet PCI requirements, you can't process cards. The standard is prescriptive: specific encryption algorithms, specific log retention periods, specific testing frequencies.
The Health Insurance Portability & Accountability Act (HIPAA) governs protected health information in the US. APIs that transmit patient data must implement access controls, audit logging, and encryption. The regulation doesn't specify exact technical controls—it requires "reasonable and appropriate" safeguards—but OCR enforcement actions have established expectations. Unencrypted PHI transmission via an API is indefensible. Missing audit logs are a finding. The regulatory flexibility means you need to document your decisions and justify them.
The EU General Data Protection Regulation (GDPR) applies to any API that handles data from EU residents, regardless of where your servers are located. The relevant requirements for APIs include data minimisation (don't return more fields than necessary), purpose limitation (don't use data beyond stated purposes), and subject access rights (APIs must support data export and deletion requests). Consent mechanisms also flow through APIs—if you're collecting consent via an app, the API is how that consent gets recorded and checked.
SOC 2 isn't a regulation; it's an audit framework. But enterprise customers increasingly require it before integrating with your APIs. The Trust Services Criteria cover security, availability, processing integrity, confidentiality, and privacy. For API providers, this typically means demonstrating access controls, change management, incident response, and monitoring. Type II reports require evidence over a period (usually 6-12 months), so you can't cram for it.
NIST SP800-228 is a specific set of security controls that the National Institute of Standards and Technology (NIST) provides for APIs. While NIST frameworks do not carry direct legal force, they are influential, informing how heavily regulated industries interpret their security obligations. This specialized document guides organizations in implementing the necessary safeguards, such as Identification and Authentication (IA), Access Control (AC), and Audit and Accountability (AU), directly within their API development and deployment lifecycle, making it an essential reference for those selling to government or regulated sectors.
ISO 27001 is a certifiable standard for information security management systems. It doesn't prescribe specific API controls, but it requires you to identify risks and implement appropriate mitigations. If APIs are in scope for your ISMS (and they should be), you'll need documented policies, risk assessments, and evidence of control effectiveness.
In practice, most organisations face multiple overlapping requirements. A healthcare company processing payments from European customers must comply with HIPAA, PCI DSS, and GDPR simultaneously. The controls overlap significantly (encryption, access control, logging, and monitoring appear in all of them), but the documentation and audit requirements differ. Build your API security program around the strictest applicable standard, and map your controls to the others.
API Security Best Practices
API security isn’t a single tool or control. It’s a set of processes and tools applied throughout the lifecycle of your APIs. Effective API security must address both the introduction of risk and the exposure of risk.
Secure API Development
API security starts with building secure APIs, and secure API development starts with designing security in from the beginning, not layering it on after deployment. APIs should enforce strong authentication and authorization by default, using well-defined identity scopes and least-privilege access to limit what each client can do. Input validation and schema enforcement are critical at the API layer to prevent injection flaws, mass assignment, and unexpected data exposure. Just as importantly, developers should assume APIs will be abused at scale and design with rate limiting, throttling, and predictable error handling to reduce an attacker’s ability to probe and exploit behavior.
Equally important is making APIs observable and maintainable over time. Clear versioning, explicit deprecation policies, and comprehensive logging help teams detect misuse, investigate incidents, and roll out fixes safely. The goal of secure API development isn’t perfection; it’s reducing the blast radius of inevitable mistakes and ensuring that when something goes wrong, it’s detected quickly and corrected safely.
API Discovery
At its core, API discovery involves identifying, cataloging, and documenting all APIs within an organization, both internal and external. This process is essential for maintaining a secure and efficient API environment.
"....60% of enterprises will lag in their digital transformation initiatives due to the lack of API discovery capabilities...”
- Gartner
In most organizations, it's impractical for any individual to keep track of every API. It isn't surprising that there is a problem with “rogue APIs.” APIs may be introduced without documentation, i.e. shadow APIs. They may be retired without updating documentation, creating orphan APIs. APIs that are supposed to be removed, but continue operating are zombie APIs. The objective of API Discovery is to create a complete, current inventory of the APIs within an organization.
Effective API discovery requires:
- Continuous, automated discovery of API endpoints
API Discovery can’t be a one-time operation. It must be continuous in order to capture the most current state of the environment and identify changes as they happen.
- Identification of rogue API endpoints (shadow, orphan, and zombie)
API governance requires matching the actual state of the environment to the desired state, and that means identifying endpoints that should and shouldn’t be present.
- Support for API protocols (REST, GraphQL, gRPC, SOAP, and WebSockets)
API Discovery that doesn’t support the protocols in your environment leaves critical blind spots. If you can’t identify it, you can’t effectively protect it.
API Security Posture Management
Often combined with API Discovery, API Security Posture Management is the practice of assessing your discovered APIs for risk. Creating an inventory is an important step, but API security is ultimately about reducing risk. API Security Posture Management encompasses the practice of identifying the most at risk API endpoints in order to execute effective mitigations. For example, APIs are designed to share data; understanding which endpoints expose sensitive data is a key component of API Security Posture Management.
Effective API Security Posture Management requires:
- Effective API Discovery (See above)
In order to effectively assess your API security posture, you need the foundation of effective API discovery.
- Continuous detection and identification of sensitive data in API traffic.
Understanding where sensitive data is in use across your API landscape is critical for mitigating sensitive data exposure.
- Automated and manual identification of business flows.
Discovery isn’t just about an inventory of endpoints. It should also provide the ability to identify the associated business flow for the APIs in use.
- A configurable API risk score.
API Security Posture Management tools should give you the ability to filter and sort by a meaningful risk score.
API Protection
75% of enterprises are experiencing API-related security incidents due to inadequate real-time safeguards.
- Outshift by Cisco
Put simply, API protection is the ability to stop attacks in real time. While detection is important, it’s not enough to simply detect an attack. You must be able to block attacks before they cause damage. API Protection provides the enforcement mechanisms that prevent attackers from exploiting vulnerabilities, logic flaws, or misconfigurations. It supports outcomes such as preventing breaches, ensuring uptime, and protecting revenue.
Effective API Protection requires:
- Inline blocking of malicious requests
Protection requires more than just detection; It requires blocking of malicious activity. Timeliness and latency are key factors in effective blocking.
- Support for multiple API protocols (REST, SOAP, GraphQL, gRPC, WebSockets)
Blocking must support full request parsing for the API protocols in your environment. Tools that are limited to only request/response headers, or limited depth are insufficient.
- Dynamic detection of both stateless and stateful attacks
API Protection tools must be able to identify both stateless and stateful attacks. That means monitoring behavior inside of API sessions.
- Flexible blocking options at the level of individual requests, sessions, or IPs
Blocking attacks requires precision and flexibility to be effective. Simple attacks require blocking individual requests. Malicious IPs should be blocked entirely. Complex attacks require blocking individual sessions. It’s critical to ensure legitimate requests are not blocked.
- Detection and blocking of behavior-based API Abuse
API Abuse, such as account takeovers and data scraping, are critical threats impacting businesses today. API Protection must detect and block these types of attacks.
- Detection and blocking of Business Logic Abuse
Business logic abuse is the new frontier of API attacks, but it’s fast approaching mainstream. Business logic abuse detection should be built on the foundations of stateful attack detection.
API Security Testing
API Security Testing aims to identify vulnerabilities and remediate them before attackers can exploit them. This is not just about static code analysis. It’s about testing APIs in the ways attackers actually interact with them. For organizations, testing supports outcomes like reduced breach probability, faster development cycles, and improved DevSecOps maturity.
- Threat Replay testing to simulate real-world attacks
Security testing can be overly artificial. Connecting security testing to real-world attacks provides an important check in the process to ensure that tests are applicable.
- Schema-Based testing
Generating API security tests based on a schema or specification ensures that all known parts of the API are tested. This testing should be paired with threat replay testing for comprehensiveness.
- Integration into developer workflows
Security testing pre-production is the most effective way to remove risk before it’s exposed. API security tools should integrate with your development environment to be effective.
- Coverage for both stateless vulnerabilities and business logic flaws
Incomplete testing tools leave gaps, and gaps in testing leave exposed risk. While no tool is perfect, ensuring that your testing tools provide adequate coverage is a key requirement.
AI Security is API Security
The development and deployment of generative AI deserves special attention when it comes to API security. The reality is that AI apps and agents run on top of APIs, making AI-APIs a key type of API to protect. Conceptually, the core best practices don’t change when considering AI-APIs, but just as we saw some special considerations with different API protocols, different types of AI-APIs should be accounted for in any API security program.
Concrete Next Steps
When it comes to building an effective API security program, where you start really depends on where you are today. The best approach is to assess your current state against the best practices outlined above. If improving your ability to discover APIs, block API attacks, or test your APIs is an area for improvement, then a demo of Wallarm is worthwhile.
FAQ
References
Subscribe for the latest news