Step-by-Step Guide: Implementing Your KYC API
Leverage a bespoke API, engineered specifically for Identity Verification (IV) as part of Know Your Customer (KYC) protocol, to increase the precision and pace of customer identity validation. The customized KYC API creates a functional bridge between your app and identity validation service.

Drill Down on KYC API Capabilities
From a feature viewpoint, this tool is a powerhouse. It modernizes the analysis of client data by replacing manual procedures, and curtails potential inaccuracies.
- Customer Data Accumulation: This API is adept at accumulating client's legal name, domicile location, and birth date.
- Data Validation: The amassed data is juxtaposed with reliable references, assuring validity of obtained results.
- Risk Analysis: It evaluates potential perils linked to a customer using insightful, data-backed metrics.
- Regulatory Adherence: An inbuilt mechanism certifies that customer data aligns with mandatory legal stipulations.
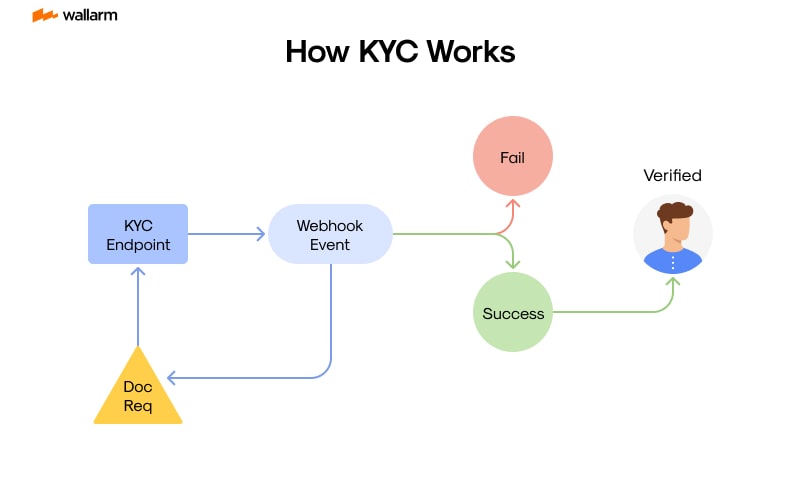
Points to Ponder for KYC API Incorporation
Target precision before embedding the KYC API into your operations.
Souring a Premium KYC API Service Provider
Service providers in the KYC API realm differ in terms of service range. Prioritize those who accentuate precision, promptness, legality, and consumer support.
- Accuracy: Target service provider's that value precision in data validation.
- Speed: Choose APIs built for expedited data analysis and validation.
- Legal Compliance: Confirm that the service provider functions within legal parameters.
- Consumer Support: Aiding client services add an extra dimension to your vendor selection.
Master API Instructions
Acclimatize with the valuable API instruction manual. It provides critical clarity on the norms of API use, features, response categories, return procedures, and arguments.
Assess Your Technical Know-How
Incorporating a KYC API requires coding proficiency and API harmonization skills. You might need expert developers or an API embedding platform, in case you lack these skills.
Protecting Customer Data
As you will be dealing with confidential customer data, it is imperative to focus on data protection. Make sure, the API incorporates robust protection mechanisms and employs encryption methods to guard data against potential breaches.
Tweak Your System Prior to Incorporating KYC API
There are a few stipulations you need to adhere to before the integration phase.
Cross-Compatibility Confirmation
Ensure that your system can:
- Accommodate the API's language.
- Host the API on your server.
- Archive customer particulars on your database.
Use an API Key for Authentication
Acquiring an API key is vital. This singular cipher enables the KYC API to grant access to your application.
Conduct a Mock Drill
Elements of preparatory integration include setting up a simulation environment to test the API. It helps diagnose potential issues and rectify them before actually integrating the API.
Deciphering Your Necessities
Kickstart your journey by clearly comprehending what your enterprise indeed requires. This entails familiarizing yourself with the consumer group you cater to, identifying the data needed to be collected, and determining the intensity of the required verification.
Pinpointing a Suitable KYC API Provider
A wide array of KYC API providers flood the market; hence, identifying a provider that caters to your unique needs forms a vital part. Weigh in aspects such as the simplicity of the integration procedure, robustness of the information protection measures, degree of compliance with set regulations, and whether they value for money.
Melding the KYC API
With your choice of provider determined, shift focus to the integration of the KYC API into your pre-existing framework. Execute these steps:
- Deriving an API Key: The onset of the integration procedure is the derivation of an API key from your selected provider assuring unique authentication of your API requests.
- Establishing API Endpoint: Follow up by establishing the API endpoints, i.e., the specific URLS receiving your API queries.
- Accumulating Essential Customer Data: Gather the requisite customer data, forwarding it to the API endpoint. This data encapsulates personally identifiable information such as full name, domicile details, date of birth, along with proof of identification details including passport number or driving license.
- Managing the Response: On secure sending of the data, the API conjures up a response. Appropriately manage this, generally done through extracting and securely storing the information.
Here's a brief Python configuration to envision the procedure:
Trial and Authentication
Post-integration demands thorough and exhaustive system analysis to ascertain if it functions optimally. This comprises checks on data accuracy, swift verification, and managing diverse response scenarios.
Continual Supervision and Upkeep
Successful KYC API integration demands constant surveillance of its performance coupled with frequent upkeep. This includes timely updating the API key when called for, responding to any shifts in API endpoints, and ensuring the protection of the collected information.
Bulletproofing Data with Client Verification API
Shielding Vital Data
The critical focus in operating client verification API is combatting illicit activities by securing customer information. This includes:
- Transmission Security: Enable encryption to secure data exchanges within your client verification API, thus making unauthorized penetrations challenging.
- Access Management: Implement rigorous mechanisms of access control. Only authorized personnel should be given entry to client verification details.
- Regular Security Assessment: Carve out a schedule for frequent safety audits to identify and resolve possible vulnerabilities.
Flexible API Alternatives
The expansion of your venture necessitates larger client verification needs. Useful methods to this involve:
- Scalable API: Choose an API that can handle mounting data load without compromising on efficiency or precision.
- Integration Capability: Your selected API should effortlessly mesh with your current system and support new functions or services that match your business's evolution.
Respecting Regional Regulatory Parameters
Understanding local regulations related to client verification procedures is essential. Suggestions for this comprise:
- Global Uniformity: If your enterprise operates worldwide, the API should uphold regulatory compliance across all areas of operation.
- Adaptive Updates: Legal norms may shift periodically. A client verification API that regularly updates to be in line with present laws is a superior choice.
Balancing Robust Security with User Satisfaction
Striking a balance between stringent security practices and enjoyable user interaction in your client verification processes is vital. This demands:
- Promptness: Choose a client verification API renowned for its speed. Lagging response times can annoy users, leading to abandoned transactions.
- Uncomplicated Navigation: The client verification process should be straightforward to steer through. Complex procedures might deter users from finishing them.
- Transparent Communication: Users should be informed about why their information is needed and how it will be used. This habit bolsters user confidence.
Perpetual Enhancements and Vigilance
Staying synchronized with the financial and tech sector's advancements is crucial. Several tactics for this cover:
- Staying Informed: Keep tabs on contemporary trends and progression in client verification technology and legal requirements.
- Seeking User Input: Regularly solicit feedback from users and use this information to upgrade your client verification processes.
- Unending Refinement: Persistently strive for improving client verification measures. This could include adopting novel technologies, fine-tuning current methods, or training your team to proficiently handle client verification procedures.
Roadblock 1: Harmonizing with Existing Infrastructure
In the journey towards KYC API incorporation, many practitioners grapple with issues surrounding the proper fusion with existing systems, unavailability of adequate technical skills, or insufficient API guidelines.
Tackling the Situation:
A thorough examination of the API guidelines is a prerequisite prior to initializing the incorporation procedure. This confirms alignment with legacy systems and verifies that sufficient technical acumen is in place for a seamless transition. In scenarios where the guidelines prove insufficient, seek further enlightenment from the API provider.
Roadblock 2: Safekeeping Customer Data
Preserving the sanctity of sensitive customer information is paramount in undertaking a KYC API journey. The repercussions of security breaches are disastrous.
Tackling the Situation:
Your selection of KYC API should be dictated by its adherence to all data safety standards. Strengthen your fortifications by adopting robust data safety measures including encryption and secure storage. An occasional security audit will ensure the fort is breach-proof.
Roadblock 3: Ensuring Seamless Customer Interaction
An ill-planned KYC API journey leads to subpar user experiences, potentially driving customers away from completing the KYC process, resulting in lost opportunities.
Tackling the Situation:
Pilot testing the KYC API before unveiling it to customers will catch any snags in the system. A straightforward, and hassle-free KYC process will motivate customers to see it through without abandon.
Roadblock 4: Regulatory Adherence
Non-compliance with KYC's regulatory requirements is a road to penalties and a tarnished brand image.
Tackling the Situation:
Being in-the-know of all KYC related regulatory prerequisites is necessary. This should prompt regular assessments and subsequent alterations to your KYC systems, ensuring they are in line with norms. A KYC API with built-in automated regulatory checks could greatly simplify matters.
Roadblock 5: Capability to Expand
As your business expands, your KYC system must keep pace, else face system overloads and other repercussions.
Tackling the Situation:
Select a KYC API that caters to substantial request volumes. In addition, a periodic review followed by suitable adjustments to your system will ensure it can handle the growth in demand.
Unveiling how FinTech Corp bolstered its operations with KYC API Integration
FinTech Corp, a disruptor in the digital banking world, employed KYC API for an elevated business setup. This digital platform required an upgraded system to verify client identities, while adhering to all regulatory norms. The antiquated KYC methods that were both laborious and error-prone, created the need for efficient solutions; elected was the KYC API.
Details of FinTech Corp's KYC API Execution
The start-up chose a multifaceted KYC API solution equipped with characteristics like risk calculation, identity affirmation, and document validation. The process consisted of the following stages:
- Incorporation of API: To interface the KYC API with FinTech Corp's pre-existing system, they had to establish the API touchpoints, configure authentication and evaluate the API requests.
- Tailoring: The KYC API was modified to mirror FinTech Corp's requirements, which amounted to setting up authentication guidelines, determining risk factors, and altering the user interface.
- Validation and Rollout: A rigorous assessment of the KYC API was conducted to certify its operationality and dependability. Post successful evaluation, the API was launched into the operational environment.
Implications of FinTech Corp's KYC API Implementation
The incorporation of the KYC API pivotaly altered FinTech Corp's operations alongside enriching customer interactions:
- Augmented Productivity: Thanks to automation, KYC procedures became simpler and swifter, truncating the client onboarding duration.
- Bolstered Compliance: FinTech Corp was able to fulfil all regulatory obligations, courtesy the KYC API. It also offered an intricately detailed audit trail simplifying compliance demonstration.
- Revamped Client Interaction: Clients could swiftly navigate through the KYC procedure, thereby improving their association with FinTech Corp.
Elevating API Security with Wallarm AASM
Recognizing the importance of safeguarding their APIs, FinTech Corp sought to intensify their security measures using Wallarm API Assault Surface Management (AASM), a server-less detection solution in sync with the API ecosystem.
The Wallarm AASM gave FinTech Corp insights into external hosts utilizing their APIs, uncovered missing WAF/WAAP solutions, located vulnerabilities, and neutralized possible API leaks. This further secured their KYC API, fortifying the date integrity and client privacy.
The introduction of Wallarm AASM was hassle-free, providing extensive insights into the security depth of their APIs. This became a cornerstone of FinTech Corp's API defense strategy, complementing their KYC API implementation.
To test drive Wallarm AASM you can avail a free trial at https://www.wallarm.com/product/aasm-sign-up?internal_utm_source=whats.
FAQ
References
Subscribe for the latest news

















