Securing API with OpenResty
Recognize OpenResty as a comprehensive, adaptive, web-focused platform established upon the tenets of NGINX and LuaJIT. It's a sophisticated assembly of an array of components inclusive of a standard NGINX core, LuaJIT, deliberately built Lua libraries, and supreme, third-party NGINX modules. The advantage of employing OpenResty is to overcome the confinement of static content delivery and pave the way to design robust, multidimensional web applications.

The Encounter with OpenResty and the Relevance of API Secure Measures
When we talk about API, which stands for Application Programming Interface, we are referring to a set of essential standards and procedures for developing interaction with multiple software. Following this, the precautionary measures for API, named API security, involve the application of specific safeguards and resources in order to protect APIs from potential vulnerabilities or breaches.
Harnessing OpenResty's strengths in the context of API security becomes a pivotal element in strengthening the safeguarding practices of web-based applications. This practice ensures that only entities with the right access can avail of these APIs, functioning exactly as they were originally intended.
The mentioned code provides an example of leveraging OpenResty to implement API protection. It utilizes the Lua-resty-jwt library to ascertain the JSON Web Token (JWT) method's authenticity, ensuring that the respective requests are furnished with correct permissions for API usage.
However, employing OpenResty in safeguarding APIs isn't just about limiting access. It also combats potential intrusions such as SQL injection attacks, Cross-Site Scripting (XSS) exploitation, and Denial of Service (DoS) assaults.
To conquer these hazards, OpenResty extends an array of modules and principles like the ngx_http_limit_req_module that facilitates rate restrictions for incoming requests, thereby preventing DoS assaults.
Implementing OpenResty for API security might seem complex, yet the right knowledge and resources can significantly enhance the fortified state of your web applications. The forthcoming chapters will take a deeper dive into this subject, offering a comprehensive guide to strengthen your API shield using OpenResty.
Underscoring the Importance of API Safeguarding using OpenResty
Today, Application Programming Interfaces, commonly referred to as APIs, serve as the backbone of the digital sphere. These indispensable frameworks foster communication among a myriad of software, becoming vital players in our current web-centric technologies. These same interconnections, however, make APIs a potential weak spot for security intrusions. Here's where the significance of a system like OpenResty comes in.
OpenResty, powered by its versatile web platform built upon NGINX and LuaJIT, ensures smooth functioning of server-side applications and robust management of API traffic, starting from the network tier up to the application stratum. What could be the reasons behind the importance of safeguarding APIs via OpenResty? Come, let’s delve into the specifics.
1. Guarding Sensitive Data: Essentially, APIs serve as gateways to critical information. In absence of sufficient security shields, cyber attackers can unlawfully tap into this information. With embedded security mechanisms like SSL/TLS encryption, OpenResty provides definitive access governance and data security.
2. Preventing API Misuse: APIs without strong security barriers are prone to manipulation and abuse possibly leading to targeted request overload resulting in a Denial of Service (DoS) attack. This is where OpenResty's rate limiting feature offers a defence.
3. Assuring Continuous Service: Any breach of your API can interrupt your service. OpenResty guarantees a steady flow of your API services by incorporating features like load management and health oversight.
4. Complying with Industry Regulations: Some sectors make it obligatory to secure APIs according to specific guidelines. OpenResty brings in wide-ranging security measures to simplify this task and ensures conformity.
5. Enriching User Confidence: Giving API security a top priority is a clear sign of your resolve to protect user data. This naturally breeds confidence and results in enduring relationships with the users.
In conclusion, OpenResty provides more than just data safety in the context of API security. Aspects like uninterrupted service provision, regulatory compliance, and user trust-building make it a holistic solution for API security. The upcoming chapter will deliver a comprehensive guide on safeguarding your API using OpenResty.
A Comprehensive Guide on Bolstering your API's Security with OpenResty
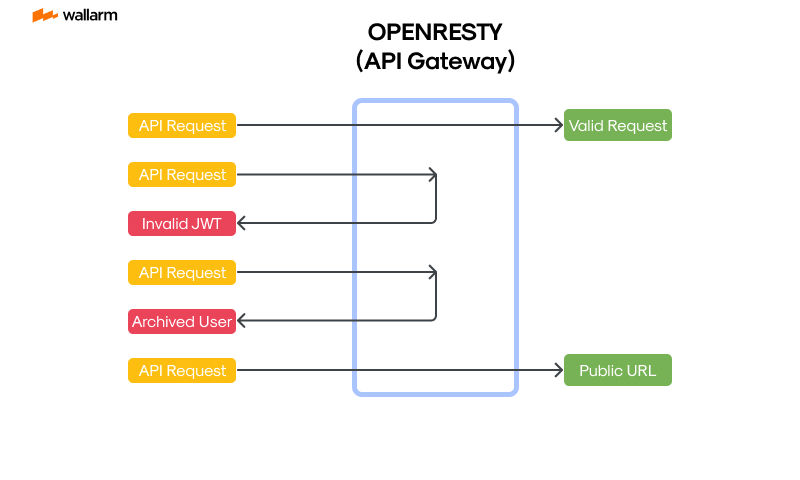
This chapter delves deep into the pragmatic techniques related to enhancing your API's security using OpenResty. We present a meticulous guideline outlining the journey of implementing OpenResty, tailoring its configuration to suit your API, and enforcing safeguarding strategies to shield your API from prospective dangers.
Process 1: Setting up OpenResty
Before fortifying your API through OpenResty, it's prerequisite to deploy it. OpenResty is a versatile web platform hinged on NGINX and LuaJIT, constructed with the motive of operating server-side web applications and APIs with increased efficiency and robustness.
Here's how to deploy OpenResty:
- Procure the OpenResty tarball from its authorized website.
- Expand the tarball running the command tar -xvf openresty-VERSION.tar.gz.
- Proceed to the expanded directory via cd openresty-VERSION.
- Initiate the command ./configure --with-pcre-jit --with-http_ssl_module.
- Wrap up by executing make && make install to compile and successfully install OpenResty.
Procedure 2: Tailoring OpenResty to Fit Your API
With OpenResty successfully installed, it's time to customize its settings for your API. This process involves creating a server block within the OpenResty configuration file and stipulating the location blocks for your API endpoints.
An overview of OpenResty configuration for your API is as follows:
In this configuration, OpenResty operationalizes on port 80, channeling all invocations to the `/api` endpoint to your appointed API server.
Method 3: Instating Safety Measures
With OpenResty installation and configuration completed for your API, it's now critical to enforce safety parameters. OpenResty proffers numerous modules to enhance the security of your API. Aggregately these include:
- Access governance: Utilize the access_by_lua_block instruction for access governance of your API. This instigates selective access to particular endpoints, depending on the IP address, authentication token, or additional parameters.
- Request pace regulation: OpenResty's ngx_http_limit_req_module lets you regulate request influx from clients to your API. This is a potential alleviation against denial-of-service (DoS) attacks.
- SSL/TLS: OpenResty facilitates SSL/TLS encryption, which can be activated using the ssl_certificate and ssl_certificate_key commands. This assures that all information transmitted between your API and clients remains secure and encrypted.
Here's a brief demonstration of security parameters in your OpenResty configuration:
The Lua code in the access_by_lua_block directive is used for access governance, setting a burst rate to 5 requests per second as rate limitation, and activating SSL/TLS encryption with a certificate and private key assistance.
Adherence to these guidelines will bolster your API's security with OpenResty shield against standard threats. However, bear in mind that security management is a persistent effort and routine vigilance, updates and revisions of your security strategies are necessary to retain their effectiveness.
Prime Techniques for Strengthening API Defense with OpenResty
API security under the aegis of OpenResty isn't about mere installation and oversight. It necessitates a repertoire of established strategies to provide a secure, efficient, and dependable API. This chapter offers a comprehensive tutorial on retaining a secure API landscape using OpenResty.
1. Frequent OpenResty
UpgradesOpenResty, akin to other software solutions, receives frequent updates to rectify glitches, enhance performance, and incorporate novelty. It's necessary to keep your OpenResty software current with all the latest safety enhancements and upgrades.
2. Embrace HTTPS
The HTTPS protocol secures communication over a computer network. It is integral for any API as it encrypts data transfers between the client and server, rendering interception impossible.
3. Regulate API Frequency
API rate regulation is a method to manage network traffic. It establishes a cap on client-request frequency to your API within a designated time span, staving off misuse and promoting equitable usage.
4. Adopt JWT for Authentication
JSON Web Tokens (JWT) are a secure method of transmitting information between parties as a JSON object. JWT makes an ideal choice for API authentication as they are compressed, self-contained, and easily transmittable via URL, POST body, or HTTP header.
5. Ensure Input Data Verification
Ascertain the validation of input data prior to processing. This preemptive step can thwart a myriad of potential attacks, including SQL injection, XSS, and external code execution.
6. Track and Monitor API Activity
Documentation and scrutiny of your API's activity can reveal abnormal patterns that might suggest potential security risks. OpenResty provides an array of modules for logging, such as ngx_lua, ngx_stream_lua, and ngx_http_log_module.
By adhering to these advanced techniques, your API's security, efficiency, and reliability can be assured. Be mindful that API security requires vigilant and routine monitoring and upgrades and isn't a set-and-forget pursuit.
Bolstering API Protection with OpenResty: Practical Illustrations
In this section, we will embark on an explorative journey into real-life examples showing the successful usage of OpenResty in augmenting API protection. These practical illustrations shed light on how various enterprises have capitalized on OpenResty to safeguard their APIs, underlining the merits and obstacles encountered during the process.
Example 1: Online Market Place
An online marketplace discovered an alarming number of API violations, leading to data exposure and financial consequences. Given OpenResty's solid safety features and adaptable attributes, they proceeded to utilize it for API protection.
The initial phase included the installation of OpenResty and adjusting it to serve as a reverse proxy for their API. This objective was successfully achieved with the following code fragment:
Within the nginx.conf file, they incorporated these lines to initiate the reverse proxy:
Subsequently, they applied rate regulation to prevent extensive force attacks, facilitated by the limit_req module in OpenResty:
The outcome? API violations in the in the online market place considerably plummeted and data security was considerably enhanced.
Example 2: Monetary Service Provider
A monetary service provider grappled with API safety issues, especially in safeguarding crucial client data. They turned to OpenResty for an effective remedy.
They introduced SSL/TLS encryption utilizing OpenResty's ngx_http_ssl_module. This measure ensured that data transfer between the client and server was encrypted and safe from interception. Below is a simplified configuration they employed:
In addition, the ngx_http_auth_basic_module from OpenResty was used for basic HTTP authentication on their API. This supplementary safety measure demanded clients to submit a username and password for API access.
The result? The monetary services provider successfully enhanced their API safety and secured their clients' confidential data.
Example 3: Digital Socializing Platform
A digital socializing platform was battling problems concerning API efficiency and safety. OpenResty was chosen due to its capacity to manage high traffic and its solid safety elements.
The ngx_http_limit_conn_module from OpenResty was exploited to limit the number of concurrent connections from a single IP, providing a defense against DDoS attacks. Their configuration was as follows:
The ngx_http_access_module from OpenResty was further adopted to restrain API access based on IP address. This facilitated the blockade of IP addresses suspected of malevolent activities.
The outcome? The performance and safety of the digital socializing platform's API were greatly improved, thereby offering a superior user experience.
To conclude, these practical examples establish the beneficial usage of OpenResty in enhancing API protection. Regardless of being an online market place, a monetary service provider or a digital socializing platform, OpenResty provides a broad spectrum of modules and features to bolster your API's security.
Navigating the Challenges of OpenResty API Security
Secure APIs with OpenResty aren't always a smooth sail. Some obstacles might put your APIs as well as your application at risk. Hence, this chapter will shed some light on these usual challenges and offer practical remedies to dodge them.
1. Neglected Rate Restriction
Rate restriction plays an immense role in ensuring API security. It curbs a single user or an IP from bombarding your server with requests that might potentially lead to a Denial of Service (DoS) strike. Nonetheless, one common slip-up is either not applying rate limitation or keeping it too generous.
The example illustrates a rate limit set at 10 inquiries per second. If this maximum is crossed, OpenResty delivers a 503 status code.
2. Overlooked Error Handling
Error handling is frequently neglected in API security. Failing to manage errors could reveal delicate information about your application to prospective hackers.
The shown example demonstrates that if some_function() malfunctions, OpenResty logs the incident and presents a 500 status code.
3. Forgoing HTTPS
Abandoning HTTPS poses a considerable security hazard. Without HTTPS, data dispatched from the client to the server isn't encrypted and is vulnerable to interception by cybercriminals.
As presented in the example, if an inquiry is made via HTTP, OpenResty redirects it to HTTPS.
4. Malpractice of User Input Validation
Disregarding user input validation can expose your system to different security threats, like SQL Injection and XSS (Cross-Site Scripting). Make it a habit to validate user input before processing.
The shown example states that OpenResty verifies if the user_input query parameter exists. If not, it sends an error message.
5. Irregular OpenResty
UpdatingFailing to routinely update OpenResty can make your application susceptible to resolved security issues prevailing in later editions. Make sure your version of OpenResty is always current.
In the given snippet, OpenResty is updated employing the apt-get package manager on Ubuntu.
Being mindful of these everyday challenges and employing the proposed solutions, you can notably reinforce the security of your APIs with OpenResty. Forge it in mind, API security is not a one-off errand but an evolving chore requiring undeviating scrutiny and updates.
Perspective Projection: OpenResty's Role in API Protection Evolution
With the continuous advancement of the digital domain, API protection strategies are anticipated to transform dramatically. OpenResty, blessed with its fortified features and adaptable framework, is predicted to have a significant role in this metamorphosis. This chapter delves into the prospective horizons of API security and estimates the function OpenResty would undertake.
1. OpenResty: Predicted Evolution of API Defense
The distinct architecture of OpenResty, a compilation of Nginx's robustness and LuaJIT's agility, positions it as a formidable weapon in API defense. Its proficiency in managing high concurrency alongside its minimalistic memory usage makes it a perfect contender for defending APIs in traffic intensive digital environs.
This code extract illustrates OpenResty's application to fortify an API touchpoint using JWT (JSON Web Tokens). The access_by_lua_block cue enables Lua code's execution for each command, delivering an exceptional level of adaptability and management.
2. Upcoming Developments in API Protective Measures
Peering into the future, several trends are likely to redefine API protective tactics:
- AI and Machine Learning: The use of advanced AI and machine learning mechanisms to identify and neutralize security threats is an emergent trend catching on. Due to OpenResty's flexible framework, it can seamlessly merge with these evolving technologies.
- Auto defenses: The automatic execution of safety protocols is a trend likely to proliferate. OpenResty's programmable nature aids in automating many security-oriented errands, including rate governance and IP barricading.
- Trust-Less Architecture: The faithless (Zero Trust) model, which inherently distrusts every entity without considering its origin, is gaining popularity. OpenResty, with its fine-grained access controlling, aligns perfectly with this security model.
3. OpenResty: A Crucial Facilitator in API Defense Evolution
Given the emerging trends, OpenResty is aptly positioned to be a crucial facilitator in the evolution of API defense. Its flexibility, performance, and programmability make it a formidable tool for safeguarding APIs in a swiftly evolving digital ecosystem.
In conclusion, while multiple upcoming trends are likely to sculpt the future of API protection, OpenResty's unique features equip it amply for steering through this constantly evolving terrain. As we march forward, it is evident that OpenResty is destined to maintain a significant role in the domain of API security.
FAQ
References
Subscribe for the latest news

















